Bipul Talukdar, Director of Application Engineering for North America
EEWeb
September 3, 2020
RISC-V is gaining attention throughout the semiconductor industry. It offers the lure of an open-source solution that anyone can leverage to create their own CPU or custom accelerator.
Of course, dig deeper and challenges emerge. RISC-V is new and does not have the benefit yet of years of field-proven experience. This means that a carefully chosen and executed CPU verification strategy is essential. It also means that the availability of a “golden reference model” is a critical component that must be secured. Without a known good reference, it is impossible to have confidence in verification results. Having a custom instruction set simulator (ISS) is vital to success.
Proper verification of a CPU design and associated instruction set architecture (ISA) is one of the most challenging activities that a CPU core engineering group must tackle. Unlike fixed-function designs or blocks, a CPU is programmable and meant to perform many different tasks. Ultimately, it is defined by the breadth and depth of its ISA and the different ways in which programmers leverage the ISA. Even using supercomputers, achieving 100% verification of the CPU considering all combinations of instructions, memory utilization, data patterns, and the like would take many thousands of years.
Instead, CPU verification groups must work smarter and focus on doing “enough” verification to catch the most likely problems. The definition of “enough” changes based on the specific CPU and ISA –– such as a broad set of capabilities versus a narrow-focused set –– and the end-application market that could be safety-critical or general-use, for example.
Large processor companies spent years and many hundreds of millions of dollars developing verification flows and methodologies for their specific processors and instruction sets. They benefit from time and experience, and even then, notable issues over the years demonstrate how difficult it is to verify CPU designs for every possible scenario.
RISC-V design and verification groups have many choices to make when architecting their methodology, flow, and toolset for CPU verification. Some groups may prefer the Accellera universal verification methodology (UVM) standard based on experience, for instance, while others may be more comfortable with C. Either approach is suitable.
Similarly, there are multiple choices when it comes to simulation platforms, a decision typically made based on either experience or the simulation platform already in use. Newer companies weigh the pluses and minuses of investing in de facto standard simulators from the EDA industry or open-source simulators such as Verilator. While no answer works for all situations, agreeing on the verification environment before moving forward is a must.
Another critical component of the flow is the CPU reference model for the chosen ISA. It may be tempting to think that it can be developed in-house, an inherently risky proposition. Developing a CPU is a huge undertaking. It is preferable to seek an outside, proven reference model, the “golden” standard against which the CPU and ISA are validated.
Outfitting the verification flow
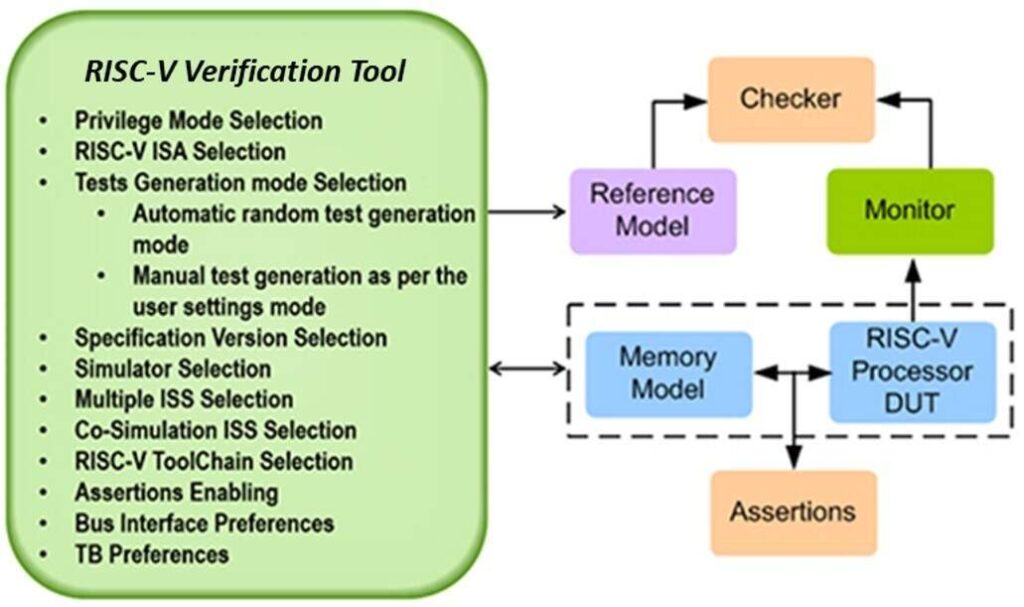
Armed with this long list of criteria, identifying a verification flow that ticks all the boxes may seem like a hopeless task. One RISC-V CPU verification platform does so as a complete environment for rigorously verifying new CPU designs based on RISC-V, specifically for RISC-V CPU developers to achieve comprehensive verification of their designs. It is compatible with SystemVerilog/UVM and C-based flows, as well as all industry-standard simulators and Verilator. Test suites for all RISC-V ISAs are supported along with proven golden reference models.
A commercial verification flow for a RISC-V CPU or custom accelerator will offer verification groups the much-needed confidence in their verification results and create open collaboration and innovation.